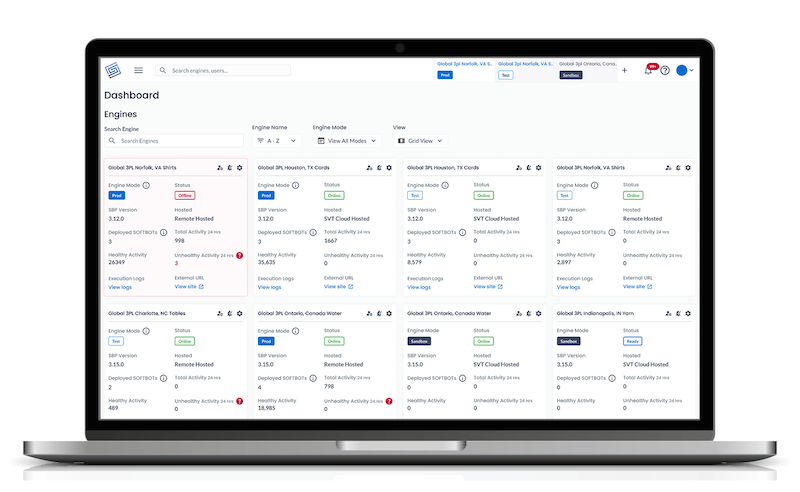
Identifying WordPress Websites On Local Networks (behind Firewalls) and Bruteforcing the Login Pages
This article explores how attackers can leverage the XSHM attack to detect WordPress sites operating…
Stop Reacting, Start Protecting Your Data
As Field CTO for Managed File Transfer (MFT) at Redwood Software, I’ve dedicated my career…
Major Cyber Attacks, Ransomware Attacks & Data Breaches
News Type Summary Report Threat actors are taking advantage of the rise in popularity of…
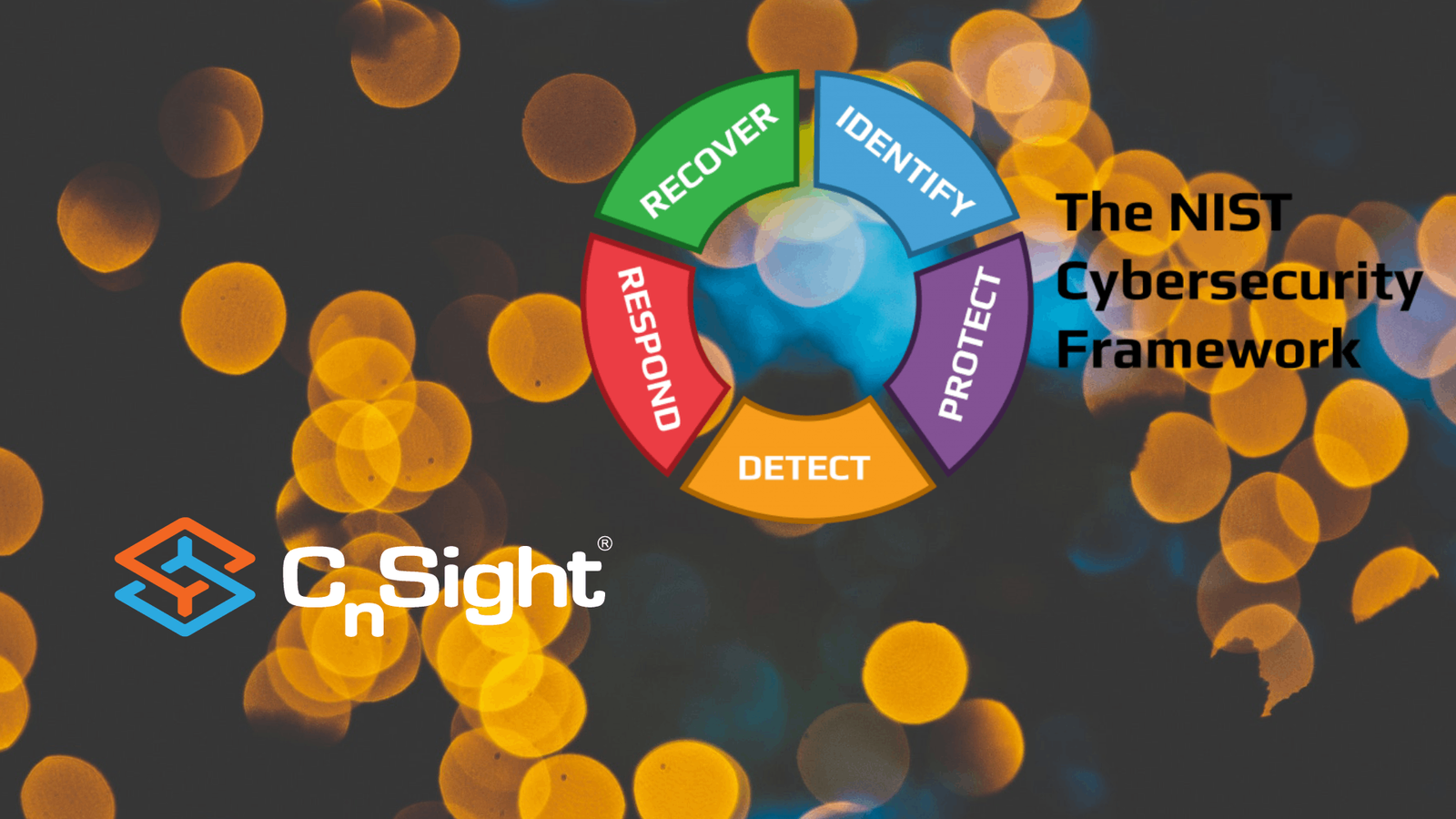
Cybersecurity Performance Management Awareness Month – How CPM helps you satisfy NIST CSF “Identify” controls – CnSight.io
To celebrate Cyber Awareness Month, we’re releasing a series of posts outlining ways Cybersecurity Performance…
PSYONIC to give live demo of its bionic technology at Robotics Summit
PSYONIC said its Ability Hand offers 32 grip patterns, with 19 pre-defined and available for…
SIEM vs IDS: Breaking Down Their Roles in Modern Security Strategies
Organizations face a growing number of cybersecurity threats that require advanced monitoring and detection systems.…
Robot Talk Episode 104 – Robot swarms inspired by nature, with Kirstin Petersen
Claire chatted to Kirstin Petersen from Cornell University about how robots can work together to…
What is an X.509 Certificate and How Does it Work?
As cyber threats evolve and become more sophisticated, securing online communication has never been more…
The Growing Demand for Intelligence Analysts in the Tech Sector
The tech industry is expanding faster than ever, creating both opportunities and challenges. Companies deal…
AI Is Reshaping Cybersecurity – Canary Trap
The rapid evolution of AI is reshaping network infrastructure and cybersecurity, driving both innovation and…