How to Renew SSL Certificate: A Beginner-Friendly Approach
If you are a website owner, then you must already be aware of the importance…
A User’s Guide to the PowerFlex 700S Series Drives
The PowerFlex 700S AC drive family supports Phase II control, leveraging DriveLogix software to combine…
Proactive Cybersecurity With CTEM – Canary Trap
Traditional cybersecurity approaches, such as periodic vulnerability scans and compliance checklists, are proving inadequate against…
Six Tips to Help You Build a Better, Safer Machine
By: Joshua Draa and Larry Reynolds, Automation Direct Safety is an essential aspect of machine…
BlackFog’s 2024 State of Ransomware Report Reveals Record-Breaking Year For Attacks
SAN FRANCISCO – 26th February 2025 – BlackFog, the leader in ransomware prevention and anti…
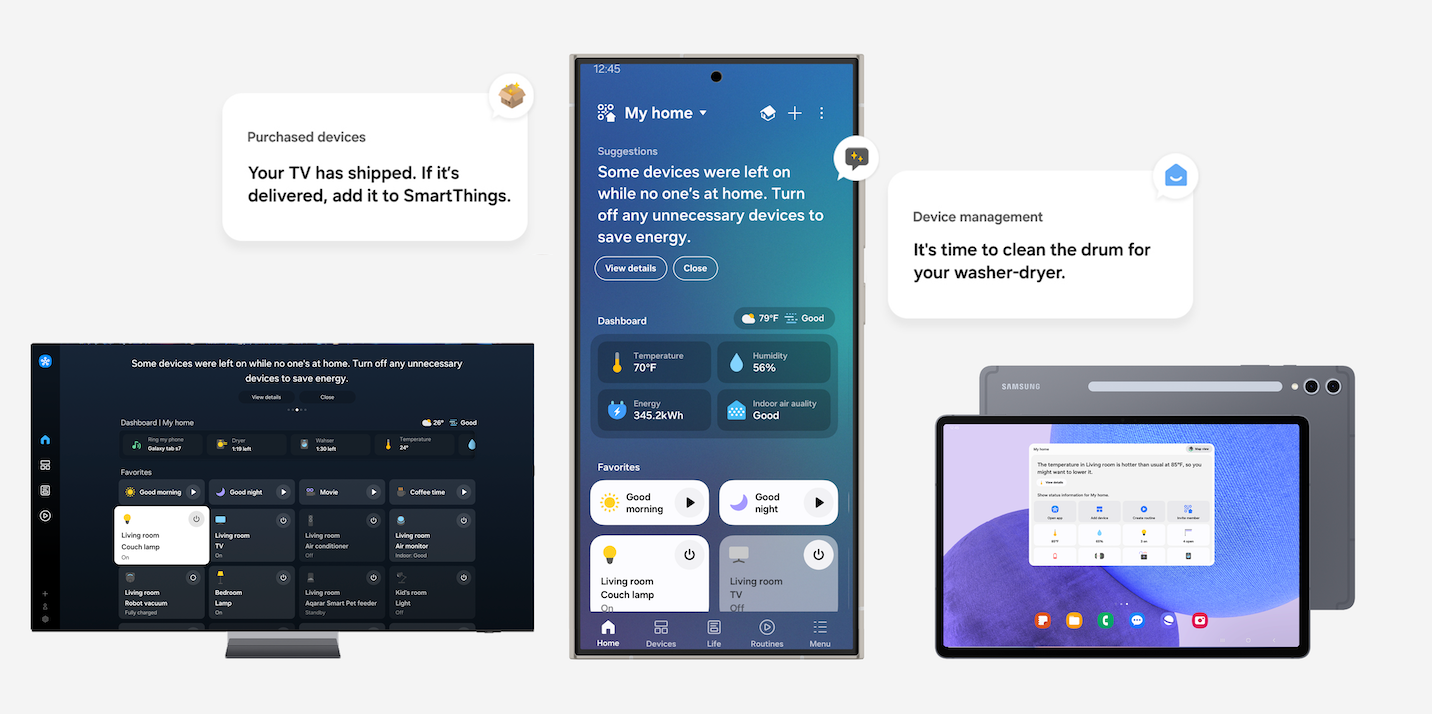
SmartThings Blog
New enhancements powered by AI offer users a more personalized experiencethrough Home Insight SmartThings has…
Homebrew Monte Carlo Simulations for Security Risk Analysis Part 2
Previously I wrote about how I had implemented the simple quantitative analysis from Doug Hubbard’s…
Why Accounting Automation Is A Must From An Ex-CFO
I remember the exact moment I knew our accounting technology was failing us. It was…
Colonial Pipeline: Lessons Learned
The Colonial Pipeline ransomware attack took down the largest fuel pipeline in the United States…
Poland Boosts Cybersecurity Amidst Suspected Russian Cyberattacks – be4sec
Poland Boosts Cybersecurity Amidst Suspected Russian Cyberattacks Poland is significantly ramping up its cybersecurity defenses…