Maximizing Throughput with the Kinetix 2000
Maximizing throughput is essential in modern automation systems, and the Kinetix 2000 series offers advanced…
Choosing the Right SOC Software: Features and Benefits to Consider
Organizations must keep pace with cyber threats, and security operations (SOC) are one of the…
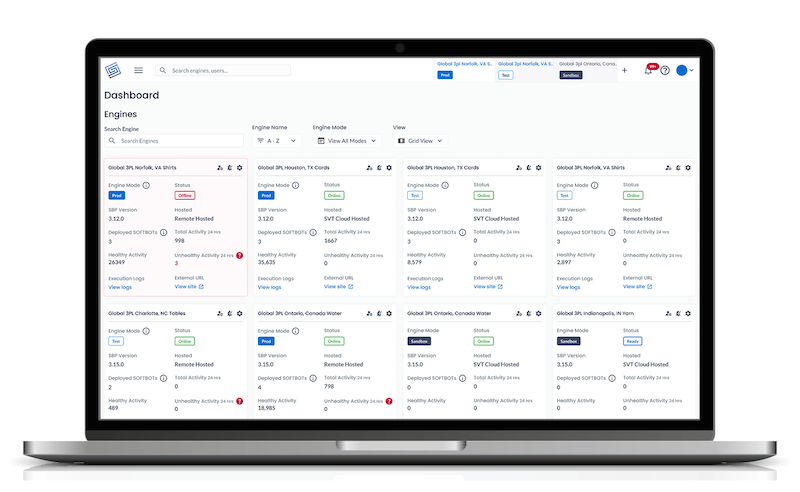
How Low-Code and No-Code Visual Programming Tools Can Simplify Industrial IoT Connectivity
In this article, we explore the transformative impact of low-code/no-code PLC programming in industrial automation…
Where to buy Wildcard SSL Certificate: A Quick Guide
In an age where online security is non-negotiable, businesses must make sure that their websites…
SmartThings Blog
Earlier this year, SmartThings announced a new program called Certification by Similarity (CbS) within its…
Canary Trap’s Bi-Weekly Cyber Roundup
Welcome to Canary Trap’s “Bi-Weekly Cyber Roundup”. At Canary Trap, it is our mission to…
Automation Training To Fill Resource Gaps
Automation technology holds immense promise for businesses, offering increased efficiency, streamlined workflows and the power…
2024 State of Ransomware Annual Report
BlackFog’s 2024 State of Ransomware Annual Report reveals record-high attacks, new variants and rising threats.…
Security Folkways and Deliberate Security Culture
Security culture remains an elusive amorphous ‘thing’ that we all aspire to improve but don’t…
10 surgical robotics companies to watch in 2025
From left to right: Medtronic’s Hugo surgical robot, Intuitive’s da Vinci surgical robot, and Stryker’s…