Mitigating Fragmented SQL Injection Attacks: Effective Solutions
This blog post breaks down Fragmented SQL Injection, a method hackers use to bypass authentication…
Supplier Profile: Master Appliance
Headquartered in Racine, WI, Master Appliance has been a leader in heat tool innovation since…
5 Common Cybersecurity Mistakes and How to Avoid Them
Nowadays, when the world is overwhelmed with cybercriminals, protecting your online assets and presence has…
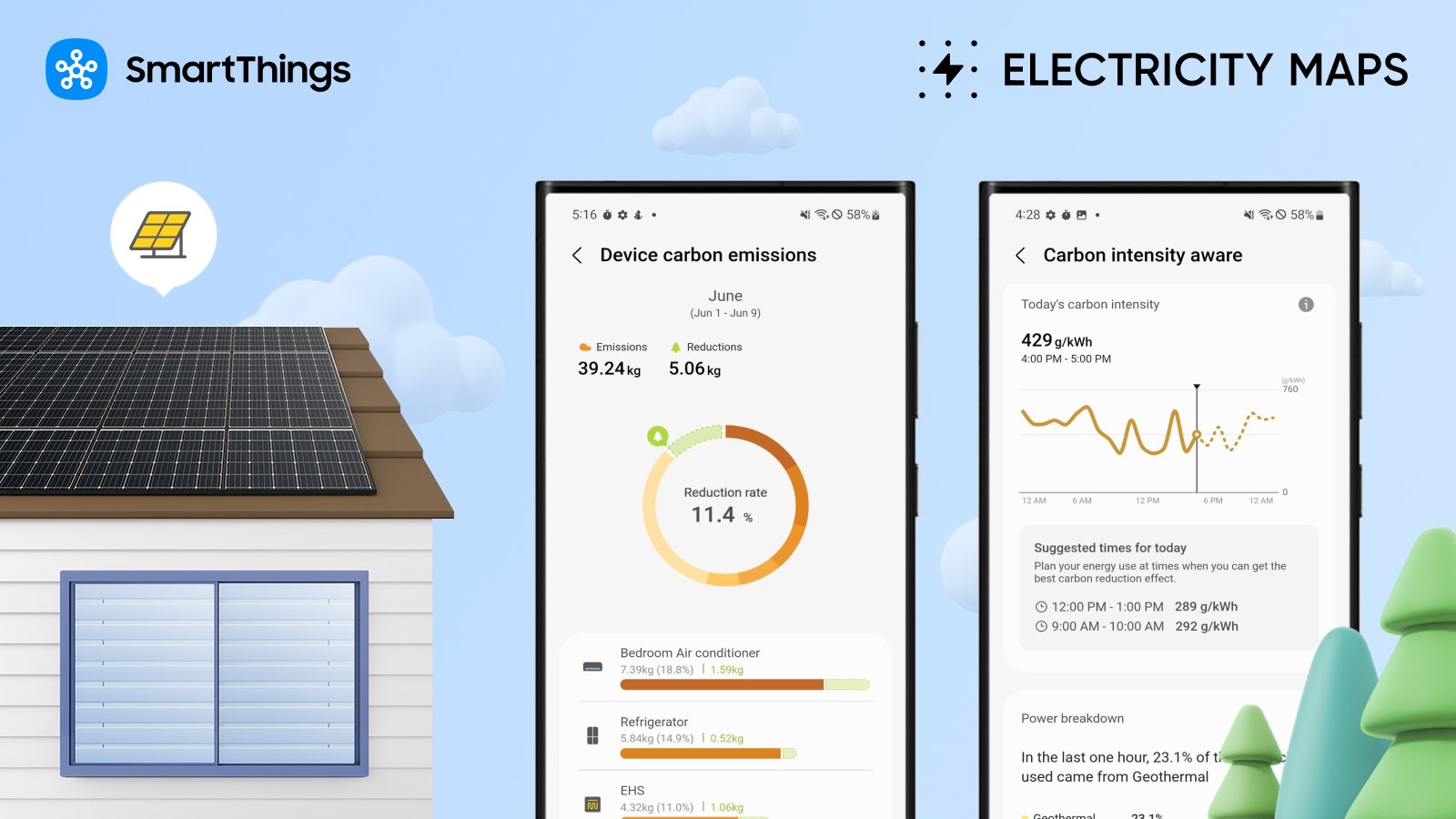
SmartThings Blog
Living a sustainable lifestyle can often be tricky. That’s why we partner with eco-focused innovators…
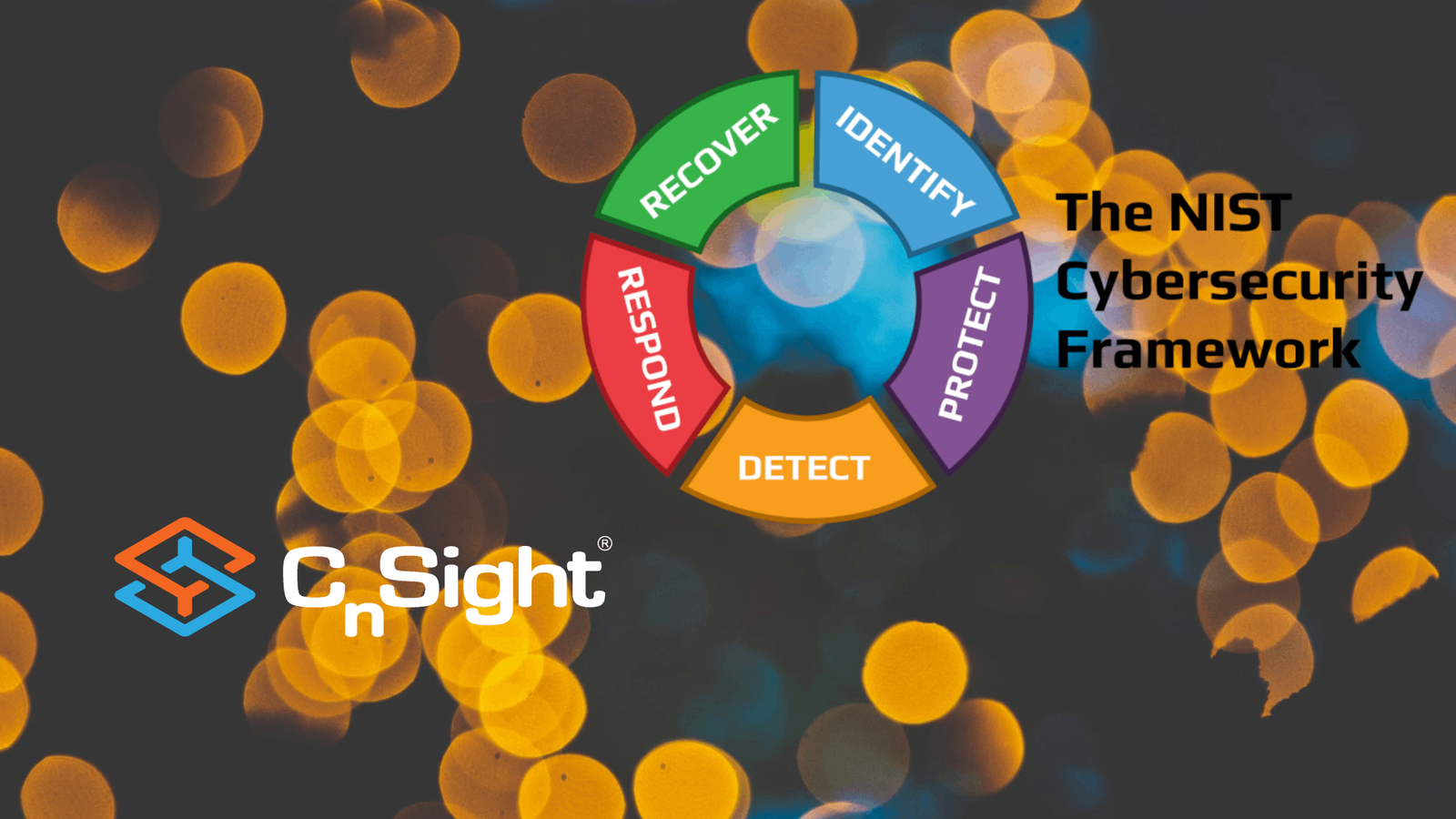
Cybersecurity Performance Management Awareness Month – How CPM helps you satisfy NIST CSF “Recover” controls – CnSight.io
To celebrate Cyber Awareness Month, we’re releasing a series of posts outlining ways Cybersecurity Performance…
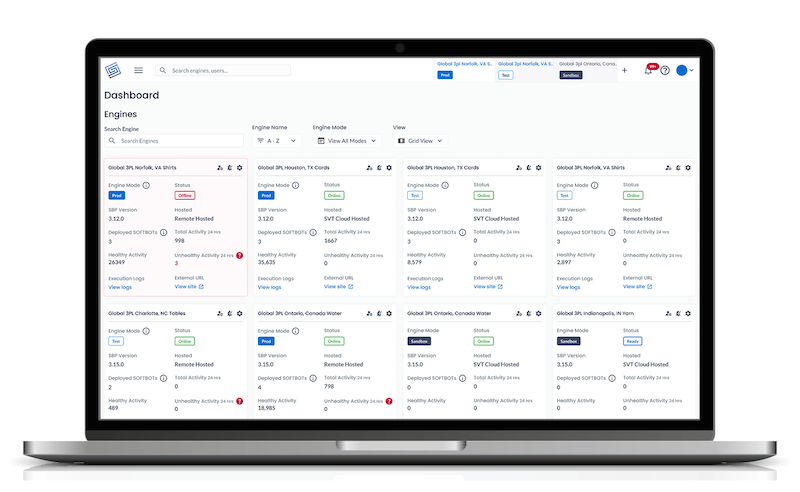
The Fortune 50’s Choice For Enterprise Automation: Redwood Software
Every household name was once a bold idea. Small teams with big ambitions, tinkering in…
MDR vs SOC: Which Cybersecurity Model Offers Better Protection?
Businesses face increasing cyber threats, making security a top priority. Two common approaches to managing…
A Complete Guide to Install an SSL Certificate on VestaCP
VestaCP is a popular web hosting control panel with an intuitive interface that simplifies server…
RISE Robotics sets sights on Guinness World Record for strongest prototype arm
RISE claims the Beltdraulic SuperJammer electric actuated arm is stronger and more precise than hydraulic…
Evolving Ransomware Tactics – Canary Trap
Ransomware gangs are adapting to stronger enterprise defenses by shifting their tactics. 75% of ransomware…