How to Choose a Sensor for the Production Environment
By: Andrew Waugh Sensors play essential roles in the modern production environment, capturing data on…
Challenges And Risks Of AI In Cybersecurity – Aghiath Chbib
Published by Aghiath Chbib Results-oriented, adaptable, established executive equipped with 20 years of success driving…
SmartThings Blog
Light up your home with SmartThings and YouTube Music The smart lighting industry is evolving…
Jen Caltrider Unwraps this Season’s Hidden Privacy Nightmare
This holiday season, privacy expert Jen Caltrider reveals how those shiny new AI gadgets under…
How 4 Industry Leaders Automated Success
Finance isn’t what it used to be, and that’s not a bad thing. The old…
Preventing CSRF Attacks with Anti-CSRF Tokens: Best Practices and Implementation
The most widely used method to prevent cross-site request forgery (CSRF) attacks is the implementation…
Role of Human Error in Cybersecurity Breaches and How to Mitigate It
While firewalls, encryption, and other tech defences bolster an organisation's cybersecurity, many data breaches still…
Navigating the U.S. robotics market: Strategies for success
In Episode 186 of The Robot Report Podcast, co-hosts Mike Oitzman and Eugene Demaitre interview…
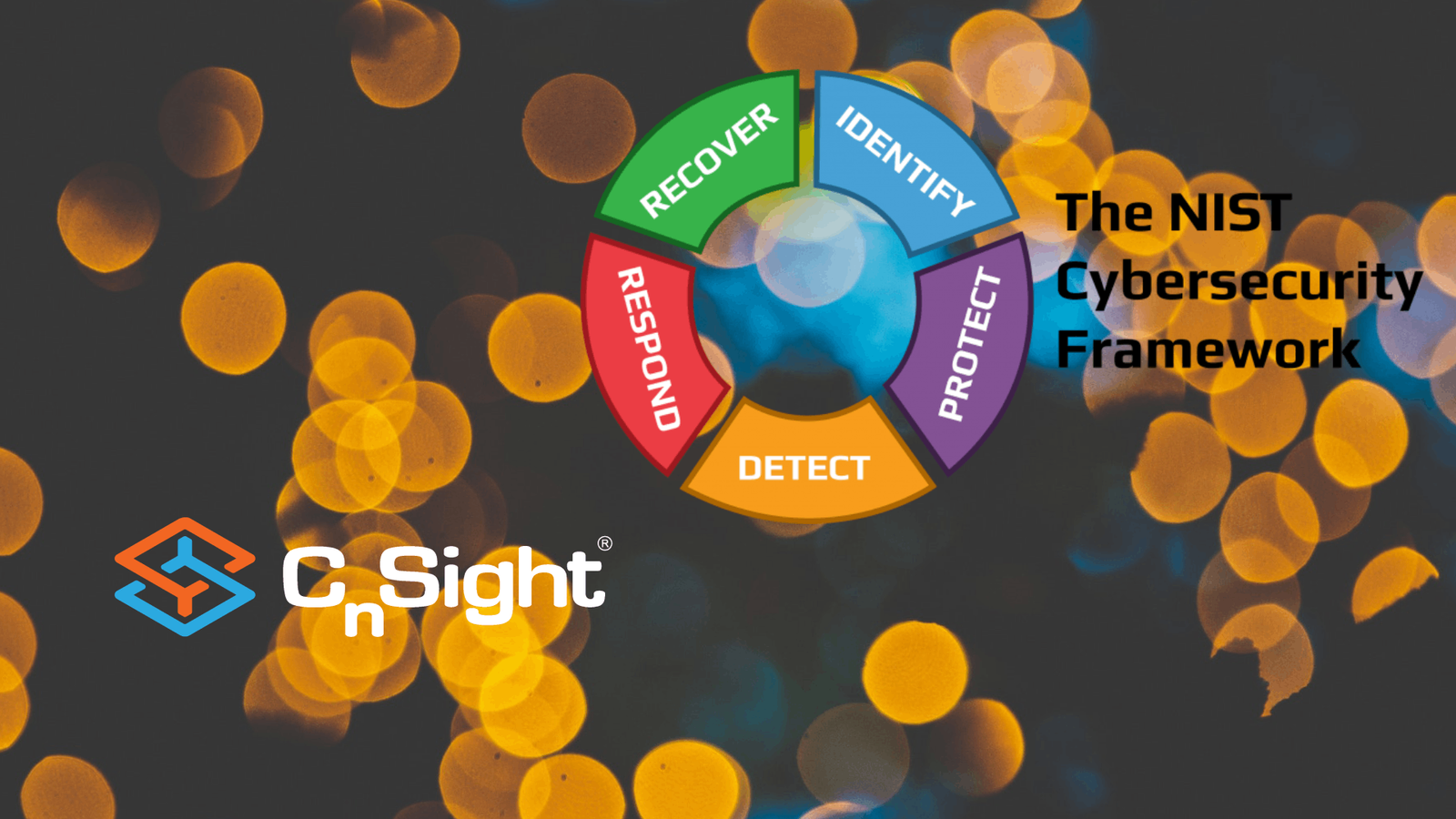
Cybersecurity Performance Management Awareness Month – How CPM aligns with the new “Govern” Security Function – CnSight.io
To celebrate Cyber Awareness Month, we’ve been releasing a series of posts outlining ways Cybersecurity…
Robot Talk Episode 109 – Building robots at home, with Dan Nicholson
Claire chatted to Dan Nicholson from Maker Forge about creating open source robotics projects you…