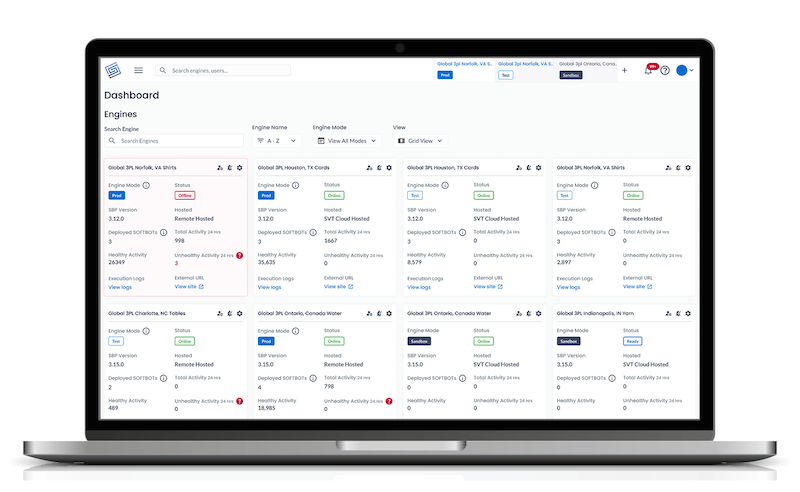
EDR Solution Comparison: Evaluating Threat Detection and Response Capabilities
Cyber threats continue to increase, making businesses need to implement strong endpoint security. Organizations use…
Google Gemini is Smarter Than You Think
Smart homes are becoming more advanced every day, and Google is leading the charge with…
How to Install a Wildcard Certificate on FortiGate?
Keeping your network safe can be stressful, especially…
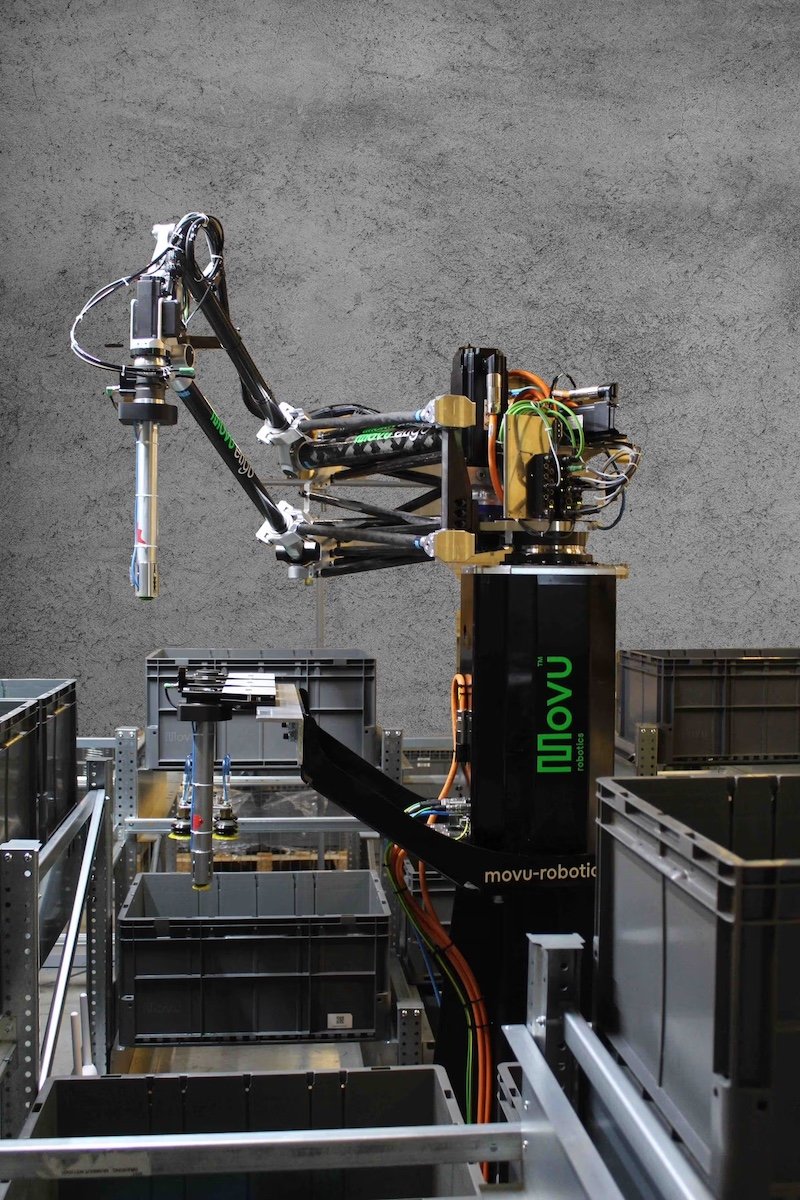
MovU Robotics and Cognibotics unveil integrated warehouse solutions at LogiMAT
Cognibotics has integrated its pick and place robot, the HKM1800, known as MovU eligo in…
AWS Phishing Exploits – Canary Trap
Threat actors are exploiting AWS misconfigurations to launch phishing campaigns using Amazon Simple Email Service…
How AI Agents Help Financial Crime Compliance Teams Re-Gain Focus
“AI” and “Focus” are two terms that rarely have a strong correlation in the countless…
DLP as a Strategy versus a Category
DLP (data loss prevention) is one of the most confusing terms when it comes to…
Compact Efficiency: The Kinetix 2000 in Small-Scale Automation
The Kinetix 2000 series offers compact yet powerful solutions for small-scale automation applications. Designed with…
Managing Identity Consciously | Black Swan Security
I had cause recently to participate in a workshop considering identity across an enterprise and…
Issue 54, 2025 | Library.Automationdirect.com
Easy, Educational, and Entertaining Automation At AutomationDirect, the goal is to educate customers on the…