log4shell — Between The Hacks
Last Update: December 28, 2021If you are reading this, you likely have heard about Log4Shell,…
The Gates Foundation’s Data Advertised – be4sec
A Chinese threat actor called lijie234 claimed that they gathered data from the American private…
Are Your Cloud Permissions Leaving You Exposed
In the rapidly evolving landscape of cloud computing, effective management of access control and…
The importance of cybersecurity in Fintech – Aghiath Chbib
Fintech companies rely mostly on their rapid adaptability to emergent changes. That is to say…
Kara Swisher Calls Out the Man Babies of Big Tech
Kara Swisher has been covering Silicon Valley since the early days, and she’s made a…
XSS Filter Evasion: How Attackers Bypass XSS Filters – And Why Filtering Alone Isn’t Enough
XSS filter evasion techniques allow attackers to bypass cross-site scripting (XSS) protections designed to block…
Disabling Directory Listing on Your Web Server – And Why It Matters
By default, some web servers allow directory listing, which means that if no default index…
Tips for Staying Safe from Cyber Crime
Nowadays, cybersecurity is something everyone needs to be aware of and vigilant about. This is…
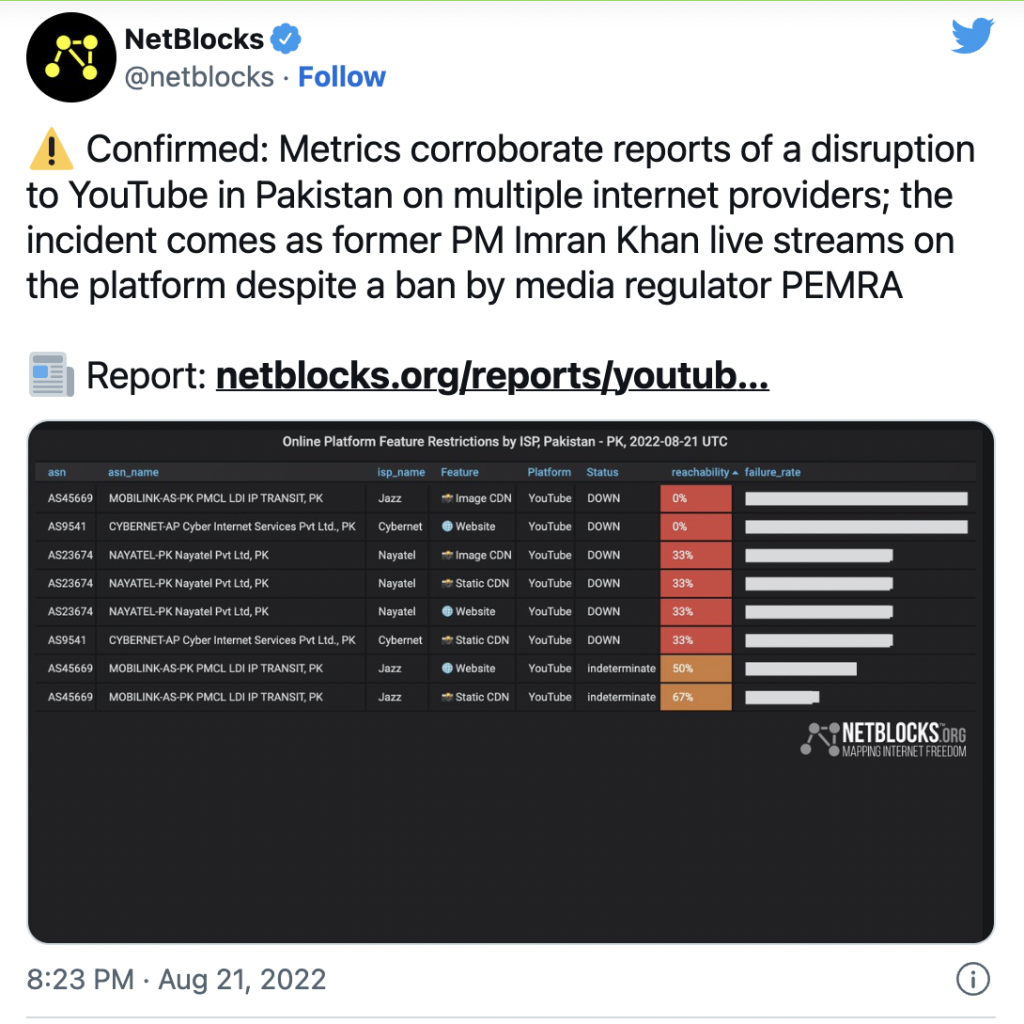
YouTube disrupted in Pakistan as former PM Imran Khan streams speech
Advertisement NetBlocks metrics confirm the disruption of YouTube on multiple internet providers in Pakistan on…
Why Small and Midsize Businesses Should Invest in Managed EDR Services
Small and midsize businesses (SMBs) are frequent targets for cybercriminals. Many attackers assume that smaller…