Strengthen Your Web Applications with HTTP Security Headers | Acunetix
What is a HTTP security header? An HTTP security header is a response header that…
5 Top Things IT Admins Need When Using About Google Chrome
Even though the famous Google product is the most used browser in the world, it…
HOW TO BECOME CERTIFIED LEAD IMPLEMENTER – ISO 27001
Advertisement ABOUT CERTIFIED LEAD IMPLEMENTER TRAINING AND EXAMINATION FOR INFORMATION SECURITY MANAGEMENT SYSTEM ISO /…
Enhancing Cybersecurity with CISA’s Cross-Sector Cybersecurity Performance Goals – CnSight.io
In today’s cybersecurity landscape, ensuring the implementation of best practices is essential for a resilient…
How Managed SOC Pricing Varies Based on Business Size and Needs
Strong security measures are necessary for businesses today as they face increasing cybersecurity threats. A…
SmartThings Blog
Now available in TX! Chances are, you’ve been experiencing some of the hottest weeks of…
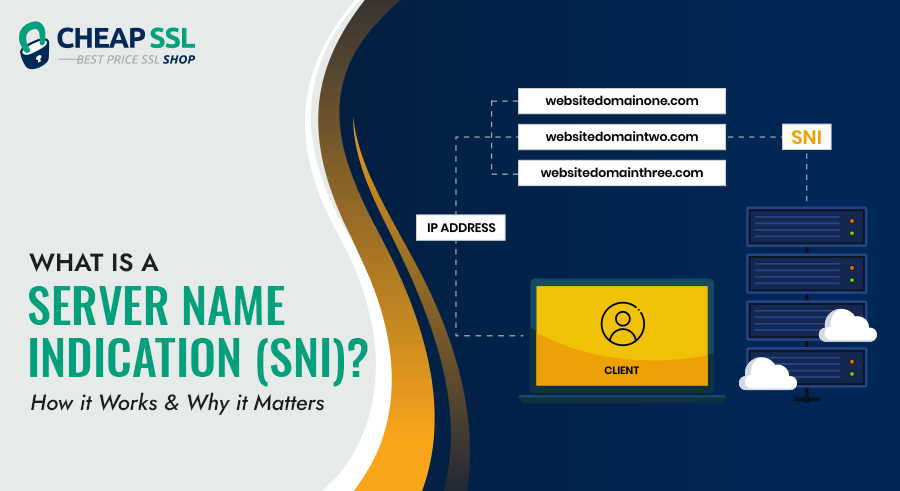
What is a Server Name Indication (SNI)? How it Works on Single IP?
Server Name Indication – SNI has changed how websites with a single IP address should…
Canary Trap’s Bi-Weekly Cyber Roundup
Welcome to Canary Trap’s “Bi-Weekly Cyber Roundup”. At Canary Trap, it is our mission to…
Continuous Data Protection: Benefits and Implementation Strategies
Continuous Data Protection: Benefits and Implementation StrategiesData is the lifeblood of every modern business, so…
What I’ve learnt writing cyber strategies with grand scopes
As part of my new role, one of my first tasks has been to develop…